
An EOS.CYBEX-Incubated Tech Firm--LianAn Found EOS Smart Contract Also Subject to Overflow Vulnerability
VaaS, a research product of LianAn Technology, has detected EOS smart contract vulnerability
SINGAPORE, April 29, 2018 /PRNewswire/ -- EOS.CYBEX is committed to building a safer EOS community, which has underpinned its supernode campaign strategy. Apart from researching an EOS-bespoke hardware cold wallet, EOS.CYBEX also pools cutting-edge industry resources and incubates entities that are highly potential to contribute to the perfection of EOS ecosystem. Recently, EOS.CYBEX's endeavor enjoyed an important harvest.
According to Chengdu LianAn (Chain Security) Technology Co., Ltd. ("LianAn Tech" below), its research product, VaaS (Verification as a Service) Platform, has identified that if a smart contract developer is not careful, EOS blockchain altcoin contract also suffers similar integer overflow vulnerability that BEC altcoin smart contact has encountered.
In recent Beauty Chain/BEC coin (https://www.beauty.io/) incidence, security hole from one line of code resulted in 0 market cap. Due to smart contract writer's lack of experience, BEC smart contract batchTransfer function has an integer overflow security hole, which was exploited by hacker(s) to fabricate 57,896,044,618,658,100,000,000,000,000,000,000,000,000,000,000,000,000,000,000.792003956564819968 BEC coins.
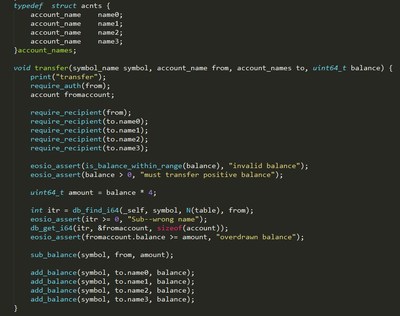
Targeting this vulnerability, LianAn Tech conducted Integer overflow vulnerability detection and security verification on EOS blockchain smart contract using its VaaS formal verification platform. It found that smart contracts on EOS blockchain are subject to similar integer overflow vulnerability. Below sample EOS smart contract illustrates this vulnerability. This sample implemented a one-to-many transfer smart contract core function "Transfer" as in fig. 1.
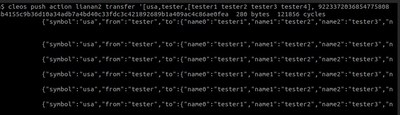
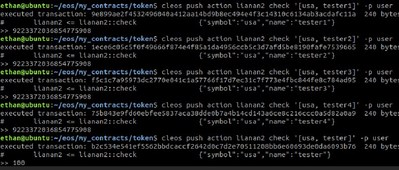
Checking above accounts after execution will reveal that sender account ("tester") balance is unchanged (100), receiver accounts (tester 1, tester 2, tester 3, tester 4) account balances are huge (2^63) due to amount overflow (Fig. 3).
Vulnerability Analysis: balance is uint64 type variable. When it is set to 2^63, because the value is less than max value of uint64, the overflow check on balance is passed. But when amount is assigned as balance*4, the overflow sets amount value to 0. Therefore, in this case amount has passed the test of minuend larger than subtrahend, then receivers' balance obtained a huge value while no decrease happens in sender's account.
So, LianAn Tech alerts developers working on EOS smart contract to pay serious attention to integer overflow and consequence that may follow. Developers should do boundary check on every step.
LianAn offers four solutions for such vulnerability issues:
- Use VaaS platform to conduct formal verification on security and functionality correctness before smart contract deployment, so that these issues could be prevented. Today VaaS plaform has supported formal verification on Ethereum, EOS, Fabric and other mainstream smart contracts.
- LianAn Tech is actively developing smart contract templates for EOS, Ethereum etc., to standardize smart contract development, to improve its security and to lower the development barrier and difficulties.
- LianAn Tech will provide community with core smart contract modules that already passed the VaaS verification. By developing their own smart contracts via these core modules, community users can reduce smart contracts security and logic vulnerability. For example, we are actively developing safe computation modules on EOS, which has passed VaaS platform formal verification (similar to Ethereum SafeMath module), so that computation vulnerability such as overflow and divide by zero could be prevented. Soon, we will develop more smart contract core function module for EOS, Ethereum and other community to cater their respective smart contract developers
- LianAn Tech proposes that smart contract developers should use Math API on EOS blockchain to prevent such overflow vulnerability. For example, smart contract developers could first convert uint type data to double type; then use double_add,double_mult and other functions in Math API for computation needs; output such computation result back in unit data at the end. In LianAn Tech experiments and tests, large value is returned and no overflow is detected when using Math API functions for large numbers multiplication. Math API usage can effectively avoid integer overflow mentioned above. But at the same time, LianAn Tech found out that Math API doesn't check negative case – if doubles computation result is negative, a wrong large value is returned when casting it into uint type. Developers should still use Math API with extra caution.
EOS.CYBEX is an experienced team dedicated to EOS project incubation and community development, aiming at providing a myriad of one-stop services for all DAPP developers based on the EOS platform, including test chains readily accessible to developers, and sophisticated test tools and services.
LianAn Tech, which has forged an alliance with EOS.CYBEX community, will dedicate itself to build a safer EOS community via its VaaS platform.
You are welcome to visit our wechat subscription account below, or email us: [email protected]
Contact EOS.CYBEX
Telegram Chinese Group:https://t.me/eoscybexcn
Telegram English Group:https://t.me/eoscybexen
Telegram Russian Group:https://t.me/eoscybexru
E-mail :[email protected]
Twitter :https://twitter.com/EosCybex
Medium :https://medium.com/@eoscybex
Steemit :eos.cybex
SOURCE CYBEX





Share this article