As Ransomware Attacks Grow in Sophistication, Both Employees and Employers are Paying Ransoms in Record Numbers
Part 2 of Intermedia's Data Vulnerability Report finds that despite organizations' best efforts to educate employees on ransomware, many still don't know what to do if they become victims
MOUNTAIN VIEW, Calif., Nov. 1, 2017 /PRNewswire/ -- Intermedia, a leading cloud business applications provider, today released Part 2 of its three-part 2017 Data Vulnerability Report, which examines the critical security behavioral habits of more than 1,000 office workers and provides guidance on how to handle them.
Ransomware attacks continue to grow exponentially
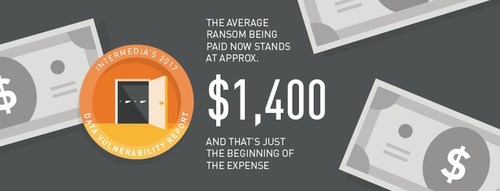
The threat of ransomware, when hackers infect devices with a virus and hold data hostage until a sum of money has been paid, is only getting worse. According to Cybersecurity Ventures, global ransomware damage costs are predicted to exceed $5 billion in 2017, which is up from $325 million in 2015. Our latest study shows that the average amount paid in ransom among office workers now stands at approximately $1,400.
Even with the increased publicity and impact of global ransomware attacks like WannaCry and Petya, and emerging strains such as Bad Rabbit, awareness still lags behind. About one-third (31%) of office workers admit they aren't familiar with ransomware. This is not for lack of effort among companies though, with 70% of office workers saying their organization regularly communicates about cyber threats and nearly one-third (30%) saying their organization specifically highlighted the WannaCry ransomware attack as an example.
Employees actions may be contributing to ransomware spike
While education helps with confidence in detecting ransomware, employees aren't always instructed on what to do if they are a victim. As a result, employees hit by ransomware may take actions that could dramatically undermine their organizations' security efforts -- and damage their bottom line. Intermedia's report found that:
- Employees shoulder costs of ransomware payments more often than employers: Of the office workers that have fallen victim to a ransomware attack at work, the majority (59%) paid the ransom personally, and 37% said their employers paid1, demonstrating employees and employers alike don't feel like there is an alternative to paying the ransom
- For those whose organizations highlighted WannaCry specifically and have been hit by ransomware, surprisingly 69% still paid a ransom themselves, further highlighting that most office workers don't know what to do if they are hit
- No one is immune from a ransomware attack:
- More than 73% of impacted Millennial workers affected by ransomware, often viewed as the most computer-savvy group of employees, report paying a work-related ransom
- 68% of impacted owners / executive management said they personally paid a work-related ransom
"Our latest report shows that, even in the face of increasing attacks, there are large gaps in overall awareness of how to handle a ransomware strike," said Jonathan Levine, CTO at Intermedia. "Employees are willing to go to great lengths to try to get data back, including paying ransoms out of their own pockets, even though 19% of the time the data isn't released even after the ransom is paid. Organizations need to focus education efforts not just on what ransomware is, but what steps employees should take if they are impacted. Regular communication is especially important right now with new malware strains like Bad Rabbit posing as seemingly harmless Adobe Flash updates. There are steps that can be taken to not only prevent these attacks from happening, but also, should one occur, to get the data back without paying the ransom. Simply put, the growth in ransomware attacks is fueled by the people and organizations willing to pay a ransom."
SMBs are particularly vulnerable to ransomware attacks
"As ransomware continues to evolve and become more advanced, organizations of all sizes and types must acknowledge it as a very real threat," Levine continued. "This is especially true for SMBs that may not have the resources, tools or training that larger organizations use to recognize, prevent and protect themselves from such attacks. Ransomware can infiltrate and shut down an entire business through just one infected computer. More often than not, SMBs feel they are forced to pay a ransom they can't, but must, afford. And hackers realize this."
What organizations should do, in light of these findings
As Intermedia's report suggests, much of the pain and agony ransomware inflicts can be prevented. Even once the initial damage is done, educated employees can still help to contain the infection by closing their computer to get it off the network. Employees need to know about the dangers of dealing with cybercriminals directly. Organizations cannot let shame or lack of knowledge drive their employees to feel like paying a ransom themselves is even an option. Simultaneously, organizations should have a continuous backup product. This will reduce the file restoration process down to minutes. Productivity won't be held at a standstill, and businesses won't need to pay the ransom in the first place.
Part 2 of Intermedia's 2017 Data Vulnerability Report provides additional eye-opening insights into the reality of how office workers handle ransomware attacks and the impact on their organizations. The report includes tips and advice for companies on how to prevent a ransomware attack as well as a step-by-step guide on how to recover should you fall victim…without paying the ransom.
This is the second part of an ongoing series. Part 3 will look at the risky data and file sharing behaviors of office workers, how sensitive information gets passed around, and the significant detriments these behaviors can cause an organization. View Parts 1 and 2 of the report, as well as sign up for a series alert, here.
Survey Methodology
This study was commissioned by Intermedia and delivered by Precision Sample®, an independent market research organization. Precision Sample has an active proprietary panel of over 3.5M respondents that is routinely validated with a stringent screening process including Verity® and RelevantID by Imperium®. Results derived from an 11-minute online survey instrument with 45 total questions, fielded June 1-5, 2017. Setup questions were used to ensure that only U.S. knowledge workers were in the sample, which was defined as those who routinely work in an office environment. Overall margin of error of +/- 2.95% at a 95% confidence interval.
About Intermedia
Intermedia offers a broad yet tightly integrated suite of cloud applications, including Unified Communications as a Service (UCaaS), business email, file backup, sync & share, identity and access management, security, and archiving – all delivered by a single provider with one point of control. Small- and medium-sized businesses want security, scalability, and someone to manage the complexities of business IT for them, and that's just what Intermedia delivers with enterprise-grade security, a 99.999% uptime service level agreement and J.D. Power-certified 24/7 support.
With more than $200 million in annualized revenue, Intermedia serves more than 110,000 business customers and 6,500 active partners, including VARs, MSPs, distributors and telecoms. Its Partner Program enables solution providers to differentiate and increase profitability by selling under their own brand. Intermedia is a leading cloud voice service provider, and the world's largest independent provider of Exchange email in the cloud. For more information, visit Intermedia.net or connect with us on Twitter, Facebook or LinkedIn.
Contacts
Melanie Lombardi
Intermedia
650.285.5857
PR@intermedia.net
Katie Halloran
LEWIS for Intermedia
619.308.5222
IntermediaUS@teamlewis.com
J.D. Power Certified Assisted Technical Program, developed in conjunction with TSIA. Based on successful completion of an audit and exceeding a customer satisfaction benchmark for assisted support operations. For more information, visit www.jdpower.com or www.tsia.com. All trademarks, service marks, trade names and product names referenced in this press release are the property of their respective owners.
1 This was a multi-select question with the other response options being 'No ransom was paid' (19%) and 'Other' (1%)
SOURCE Intermedia
Related Links
WANT YOUR COMPANY'S NEWS FEATURED ON PRNEWSWIRE.COM?
Newsrooms &
Influencers
Digital Media
Outlets
Journalists
Opted In





Share this article